7 common Big Data Security challenges and how to prevent them
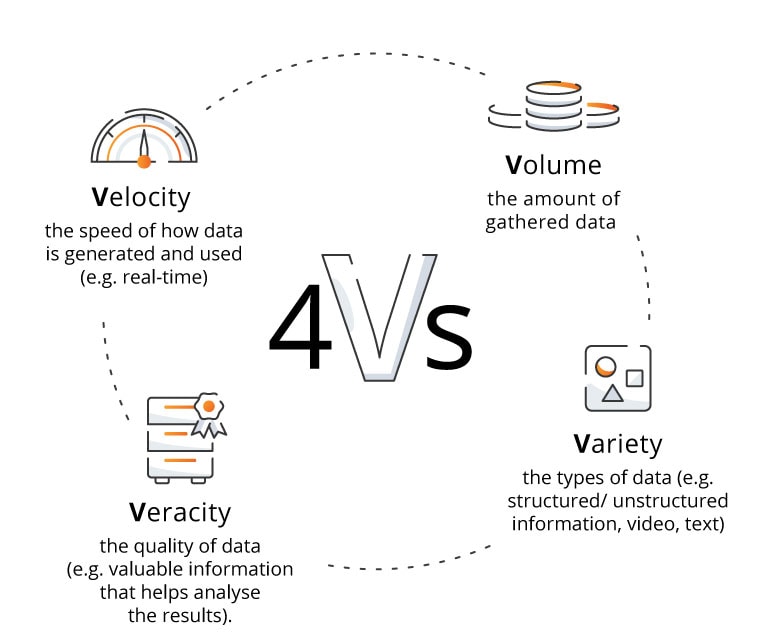
Big Data consists of sets of data that are too large, complex or numerous to be dealt with by traditional data-processing software. It is commonly described as the four Vs: Volume, Velocity, Veracity and Variety.
Big Data Security: evolving threat landscape
These days, there are quite literally billions of devices from which we can collect data.
As companies from all corners of the world make the step towards cloud computing and create their own digital transformation strategies, they are able to study Big Data available from the enormous number of IP-equipped endpoints to identify the hidden trends within.
This can benefit companies by allowing them to improve certain aspects of their business, such as customer satisfaction, swifter service delivery and higher revenues.
With all the advanced architectures that are being created to store Big Data, the threat of greater criminal activity rises.
Digital threats such as malware pose a very real risk to companies seeking to protect their information. These threats can be devastating to an organisation and cause it irreparable harm.
Many of the tools associated with smart analytics and Big Data are open source and not necessarily created with security as the number one concern, which poses big problems.
Software security is extremely important and many companies who have made the digital leap are now reaching out to consultants to stiffen up their defences in anticipation of these very real risks.
7 Big Data Security issues
We all know Big Data presents some unique security challenges. Let’s look at seven main ones to understand the complexity of this issue.
1. Data storage
Cloud data storage comes with risks and security issues that need to be carefully considered. Making any type of mistake when it comes to storing data in the appropriate location can be absolutely critical for companies, so this is an issue that needs to be looked at very carefully to avoid the data being taken.
In Big Data architecture, it is common practice for companies to take a ‘multi-layered’ approach in which they use a range of locations according to the type of data they want to store, depending how ‘sensitive’ or critical it is.
Although cloud data storage can increase the speed and performance of a company’s systems, without a cyber security expert there is a risk of threats. Therefore, not all data should be stored in the cloud. A multi-layered approach involves storing normal, everyday data safely in the cloud, but keeping the most sensitive, ‘hot’ data away from the cloud on isolated infrastructure such as flash media.
However, this does come with the cost of slower systems and processes.
You may be interested in:
2. Data management
Security breaches can be devastating to organisations and may have enormous consequences as they leave them vulnerable and compromised. It is therefore absolutely critical that businesses maintain highly secured databases so that they can ensure the security of their data as much as possible.
Companies must implement rigorous security practices and follow comprehensive software-based security measures in order to safeguard their data.
Such practices could involve using data encryption, implementing a secure on-site server, data segmentation and so on. It is also important that businesses make use of tools which monitor data sharing and notify them when any data has been compromised.
Find out more about how to use data to grow your business:
Business Intelligence: unlock the potential of your data and put it to use
Creating a data-driven culture: a roadmap for organizational transformation
3. Data access control
Controlling data access can be very tricky with Big Data.
This is because one of the biggest components involved in creating functional Big Data environments is granular access control, which involves granting different users individual levels of access to the database and its information.
While at first glance this compartmentalisation comes across as more secure, it can come at a cost.
As companies utilise larger and larger data sets, this granular access can actually become very complex when huge numbers of people have different levels of access to the systems. When there is just a small team of staff, it is easy to keep track of who has access to what information.
However, as this grows, companies open themselves to greater risks of information theft or leaks, with reduced visibility of who is responsible.
In addition, this granular access can limit key people from getting the full set of data they require to do their task properly, and can significantly slow down efficiency.
4. Fake data
If cybercriminals gain access to your database, they are able to create ‘fake data’ and store it within your system. This poses a big threat to businesses as it causes them to waste precious time and resources identifying and eliminating this fake data that could be better spent on other areas of their business.
If not identified as fake, these ‘false flags’ can cause companies to take unnecessary actions that are not needed, which can result in lowering production and spending money to fix issues that don’t actually exist.
Many organisations try to avoid this issue by relying on real-time data analytics or the IoT (Internet of Things) which help them to limit access to fake information and alert them of its presence using machine learning models which are designed to identify anomalies in their data.
5. Data privacy
Keeping data private in the modern digital word can be really difficult.
Personal and sensitive information needs to be rigorously safeguarded from cyberattacks, data loss (be it intentional or otherwise) and breaches. In order to combat this, organisations must follow strict data privacy processes in conjunction with cybersecurity and Big Data security tools.
In order to best protect sensitive data, businesses should know their data and aim to have a full grasp of all data stores, backups and networks.
It is crucial that they protect their systems as best they can against unauthorised access by carrying out frequent risk assessments and training key staff members on the importance and practicalities of data privacy and security.
6. Distributed framework vulnerabilities
In order to get full utilisation of Big Data, companies need to distribute their data analytics across multiple systems.
This helps companies to analyse Big Data on many systems simultaneously. This offers huge benefits as it results in faster analysis, but opens them up to greater risks due to the distributed frameworks. It also harms organisations as it takes them a lot longer to identify security breaches when they happen.
The CTO of Virsec, Satya Gutpa, stated:
There continues to be a temporal disconnect between the time frame for attacks versus response… Attack chains act within minutes while the time to discovery is more likely to be months. This gap must be tightened and security tools need to focus on real-time attack detection if we are to have any chance to curtail these breaches.Satya GutpaThe CTO of Virsec
7. Real-time security compliance
Real-time Big Data analytics tools have found their way into widespread usage in recent times and can be a powerful tool for a business, as they can create a huge amount of information that can be used to improve many systems and processes.
However, with this benefit comes the risk of opening up the company to greater security threats due to the volume of data involved.
Real-time security and compliance tools must be designed to not only recognise signs of data leaks and breaches, but also to identify ‘false positives’ that can lead to fake data.
If used well, they are extremely powerful appliances, but if not set up correctly, they leave themselves prone to abuse.
Benefits of Big Data Security
As we can see from the seven common Big Data security issues listed above, enterprises are right to take these potential problems very seriously indeed. The digital transformation is in full swing and nothing can change that, but it comes with a fresh set of security challenges that need to be overcome.
The main benefits associated with implementing robust Big Data security management include:
Data protection which helps maintain data confidentiality and ensures the integrity of the stored data.
Maintaining trust and reputation among customers, partners, and stakeholders.
Better regulatory compliance.
Preventing data breaches, crucial for avoiding the financial, legal, and reputational consequences associated with unauthorised access to sensitive information.
Risk mitigation which contributes to the overall resilience of the organisation.
Enhanced customer confidence which can lead to increased loyalty and positive relationships.
Business continuity and data integrity, achieved by preventing disruptions caused by security incidents.
Cost savings achieved by preventing data breaches and security incidents.
Improved operational efficiency by ensuring that only authorised individuals have access to specific data.
Early detection of anomalies which allows organisations to respond quickly and effectively to mitigate risks.
Competitive advantage.

Best practices in Big Data Security management
To ensure the highest level of Big Data security organisations need to have a well-defined strategy that will allow them to achieve their goals.
Let’s look at some best practices that will help with that.
User access control
Implementing strong access controls allows to restrict access to sensitive data. Using authentication mechanisms and role-based access controls helps ensuring that only authorised users can access specific data sets and perform certain operations.
Encryption
Encryption of data both in transit and at rest safeguards information from unauthorised access during transmission between systems and while stored in databases or data lakes.
Network security
Securing the network infrastructure supporting Big Data systems protect data during transmission.
Incident response plan
Developing and regularly testing an incident response plan allows to address security incidents promptly. A well-defined plan helps minimise the impact of security breaches and facilitates a swift and coordinated response.
Employee training
Educating employees about security best practices, the importance of safeguarding sensitive data, and the potential risks associated with data breaches is a critical component of overall security.
Regular audits: the key to continuous improvement in Big Data Security
There are plenty of methods and tools to help companies combat Big Data security issues, and more and more are being developed as time goes on.
For businesses who are unsure of where they stand in this age of increasing digital security, there are guides for safe software development and services such as software audits that can help them get on the right track.
With the right tools, information and expertise, all these challenges brought up through Big Data usage and analysis can be dealt with effectively.
When these threats are brought under control, enterprises can finally use Big Data to help them thrive and really reach their potential for harnessing data to propel their companies to areas they could only dream of before!
Regular security audits play a crucial role in ensuring continuous improvement in Big Data security. Audits provide a systematic and thorough examination of security practices, policies, and controls, helping organisations identify vulnerabilities, assess risks, and implement necessary improvements.
Who is responsible for Big Data Security in your organisation?
While it all depends on your specific situation and business, it’s always worth knowing who is responsible for Big Data Security in your organisation.
Key stakeholders who often play a role in Big Data security include:
Chief Information Security Officer (CISO), responsible for the overall information security strategy of the organisation,
Data Security Officer, who focuses on the security of data assets,
Chief Data Officer, responsible for managing and governing the organisation’s data assets,
and Data Governance Team, responsible for establishing policies, standards, and processes related to data management, quality, and security.
Apart from them your team can also include IT Security Team, Big Data Administrators, Data Scientists and Analysts and Compliance and Privacy Officers. Your Big Data team and its composition will depend on the size of your organisation and on your needs, so when in doubts do get in touch with us.
At Future Processing we can help you at every stage of developing and implementing Big Data strategy, from consultations and workshops to implementation of the final solutions. Let’s talk to see how we can help you with your Big Data security challenges!