
10 New Software Development Technologies and Trends
Software is the driving force of the world today. With an estimated 9 trillion devices in use, software is the glue that connects people from all around the globe. The developers that build and develop these products are shaping and building the modern technological world.
What are software development technologies?
Software development technologies encompass a broad range of tools, frameworks, programming languages, and methodologies that are used to create, test, and maintain software applications. These technologies are the backbone of the digital world, powering everything from simple websites to complex, cloud-based enterprise solutions.
The software development field is expected to grow to 28.7 million people by 2024. However, even with this increase, there’s still a shortage of skilled talent.
In the ever-changing world of technology, the software industry is constantly evolving. Staying updated with new technologies and innovations is crucial for software developers and professionals. This helps them remain competitive and earn better positions and salaries.
The IT industry has experienced significant growth in recent years, reflecting its dynamic nature.
Why keeping track of emerging technologies is crucial in the Software Development industry?
The evolution of software technologies provides a clear insight into the type of developments ongoing in the information technology industry. Developers all around the world are working to improve the convenience and comfort level of humans. Alongside traditional development, such as Java application development and .NET development, developers need to keep themselves updated with emerging technologies and trends.
Similarly, it is vital for organisations to adopt these new technologies in order to expand and compete with their competitors. Consultancy companies can provide greater insights into these new technologies and help businesses become software leaders.
Additionally, staying current with software development trends and emerging technologies allows companies to innovate more effectively, addressing both current and future challenges. This approach is crucial in a rapidly evolving field where user needs and technological advancements constantly change.
10 trends and latest technologies in the software industry
The technology industry is shaped by the adoption of new technologies, playing a crucial role in its future.
Here are the latest software development trends to watch out for.
Cloud Computing Platforms
Cloud computing providers are an essential part of the IT landscape and are rapidly expanding. They are predicted to achieve a market size of roughly $0.68 trillion in 2024, which is expected to more than double by 2029, reaching $1.44 trillion. This trend highlights that cloud computing is now a crucial component of the digital transformation strategy for many businesses.
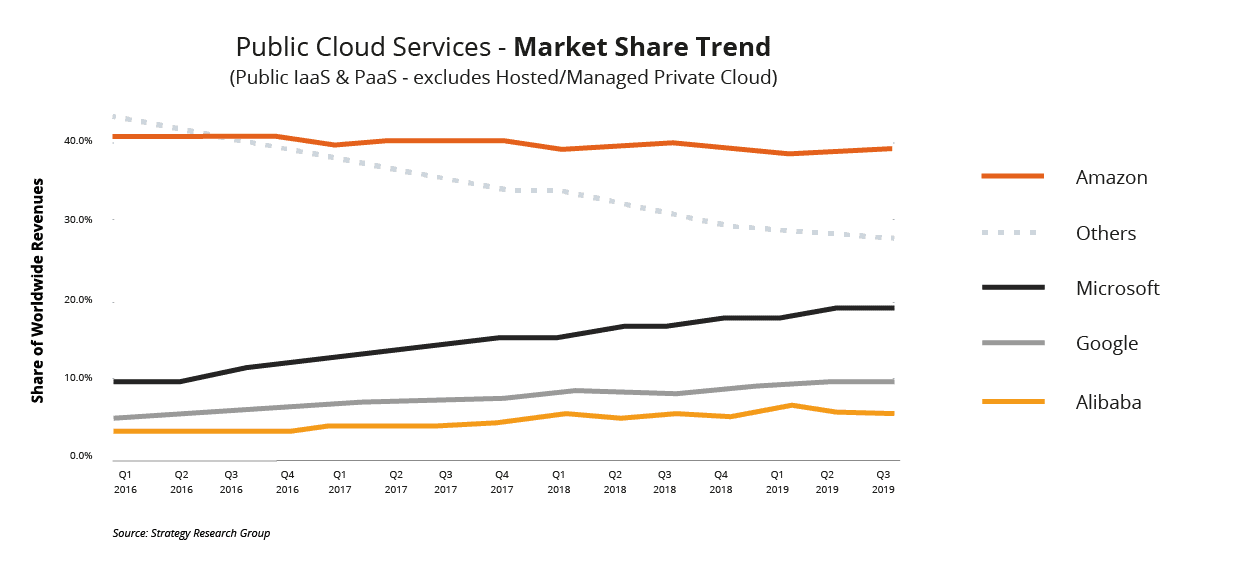
These platforms provide a range of services, such as hosting applications, storing data, and providing computing power through the Internet. They allow businesses and individuals to access and manage resources without the need for physical hardware or complex infrastructure.
Notably, they are known for their flexibility and operate on a pay-as-you-go model, which can lead to significant cost savings. These platforms can support various applications, from basic website hosting to complex data analytics, and are renowned for their reliability and advanced security features.
DevSecOps
DevSecOps is an innovative software development approach that integrates security practices within the DevOps process.
The main objective of this approach is to ensure that security is embedded in every stage of the software development life cycle, starting from the design phase to development, deployment, and software maintenance.
DevSecOps practices encourages collaboration between the development, security, and operations teams to release software more quickly and securely. While it is essential to have a shorter development cycle, security should not be compromised. This solution ensures that the security requirements are met without compromising the development.
Low-Code and No-Code Platforms
Instead of writing code by hand, developers can employ low-code or no-code platforms, which are software development environments, to build apps with configurable and graphical user interfaces.
You can build applications fast and with minimal coding on these platforms, even if you don’t have much programming experience. The market for these platforms is rapidly expanding and is estimated to reach a size of USD 16.17 billion in 2024. No-code platforms are suitable for both corporate users and citizen developers.
On the other hand, low-code solutions still require some level of coding and are, therefore, more appropriate for developers who are more experienced in the software development process. Both these platforms share a common objective: simplify application creation for everyone.
Artificial Intelligence and Machine Learning
A total of 91 machine learning deals were carried out last year, with a business value of 16.9 billion dollars. According to Deloitte, approximately 100,000 legal jobs will be automated by 2036. Automation and machine learning are here to stay. They will make a huge difference and change how organisations operate.
Machine learning allows businesses to customise the customer experience and helps target the company’s efforts. For example, Facebook implements statistical analysis and predictive analytics together to find patterns based on data.
It helps the social network personalise each individual’s newsfeed and suggest interesting content and posts, improving user experience. In addition, Facebook uses neural networks on images to suggest members to tag in the picture.
Artificial Intelligence and Machine Learning solutions aims to be able to improvise business tasks and makes them simple. The advent and popularity of artificial intelligence have provided web app developers with a brilliant means to experiment.
So far, the reach of AI has broadened into sectors like healthcare, banking and FinTech, education, mathematics, data analytics etc.
Read more:
The impact of AI on software development: opportunities and challenges
Artificial intelligence usage in multi-factor authentication
Cybersecurity in Software Development
Cyber threats are becoming increasingly frequent, and digital systems are becoming more complex by the day. As a result, cybersecurity has become a crucial topic in software development over the past few years. Robust security measures are now more critical than ever before because software plays a significant role in all aspects of business and daily life.
The software development process is evolving and placing a greater emphasis on security from the outset. This means that encryption, safe authentication mechanisms, and secure coding practices are being prioritised.
Additionally, automated testing and continuous security monitoring are being utilised to quickly identify and address any vulnerabilities.
Blockchain in Software Development
Blockchain technology is a decentralised and trustworthy solution that can be used in various applications for software development. While it was initially developed for Bitcoin, the technology community is exploring new ways to utilise it. The global blockchain market was valued at around $7.4 billion in 2022, and experts project it to grow to over $94 billion by the end of 2027.
Blockchain solutions has many potential applications in the software industry, including auditing supply chains, smart contracts, and secure transactions. Its growing popularity across sectors is due to the fact that it provides transparency, security, and a decreased likelihood of fraud.
Sustainable and Ethical Software Development
Developing software sustainably and ethically involves considering its impact on society, the economy, and the environment at every stage of its life cycle. This includes reducing software’s energy consumption, ensuring data privacy and security, promoting accessibility and inclusivity, and adhering to ethical standards during the design and deployment phases.
To strike a balance between technological progress and social responsibility, software must meet the current and future needs of users and businesses without compromising the ability of future generations to meet their own needs.
Read more:
The Impact of IoT (Internet of Things)
The Internet of Things (IoT) covers various categories of devices that are connected to the Internet and communicate with each other. The applications of IoT are present in both the consumer and the industrial domains. In areas such as security and customer experience, IoT is observing exponential growth and demands.
According to David Evan, a former researcher at Cisco, about 127 devices are being connected to the internet each second. This clearly signifies the constantly increasing reach of IoT.
Over 90% of automobiles are estimated to be IoT-enabled by 2020. In the coming years, IoT will continue to grow in prevalence and get more sophisticated. From smart cars to in-store smart assistants for customer personalisation, the future holds a lot of value for IoT.
Enterprises will come closer to an intelligently connected future by embracing real-time visibility.
Mixed Reality
Mixed reality is a combination of the two twin technologies of Virtual Reality (VR) and Augmented Reality (AR). Statista predicts that, by 2025, the market size of mixed reality will reach 3.7 billion US dollars.
AR has seen tremendous growth recently, and the credit for this lies solely in its smartphone applications. The popularity of smartphones is one of the major reasons companies are hiring large numbers of AR developers and investing in their own AR applications.
Many people assume that these applications, as well as the scope of VR itself, are limited to gaming and entertainment. However, effective applications by companies and armies around the world have proved this notion wrong.
The US Army has used Microsoft’s HoloLens mixed reality technology for military training purposes, and similarly, Walmart is also planning to utilise VR technology to train employees in customer service and compliance.
Progressive Web Applications (PWA)
Progressive web applications (PWAs) are a hybrid of mobile and web applications. They differ a lot from the regular mobile application. The service worker script is an integral part of PWAs, where they are majorly used. PWAs have a number of features, such as responsiveness, connectivity independence, safety, linkability, etc.
The main feature of PWAs includes its offline support, where the application is supposed to be able to work without a connection. These applications can be loaded very fast, even with low internet speed.
For example, Uber’s PWA was designed to run even on 2G speeds. The core app is a mere 50kB and takes just 3 seconds to load on 2G speeds. PWAs are also very good for customer engagement. Trivago saw an increase of 150% for the people who add its PWA on the home screen. Trivago also observed a 97% increase in hotel offer click-outs owing to this increased customer engagement.
Additionally, they are very easy to develop and maintain. This, in particular, has attracted many mobile developer companies in the past few years.
Embrace the future of Software Development with Future Processing
The software market is always evolving, so you need an expert at delivering innovative technology solutions to keep up.
When you partner with Future Processing, you can be confident that your projects will be developed using the latest trends and technologies, resulting in cutting-edge, innovative, and efficient solutions.
Our dedication to quality and innovative mindset make us an ideal choice for anyone looking to stay ahead of the competition in the software market.



