How to detect and fight phishing in 2022?
Phishing is an example of the most frequent and dangerous cyber attacks affecting both individuals and businesses all over the world. The global pandemic, the urge to work from home and the rapid development of online services have become an excellent opportunity for hackers to steal priceless data. Let’s find out what can be done to increase the level of security and avoid phishing soon.
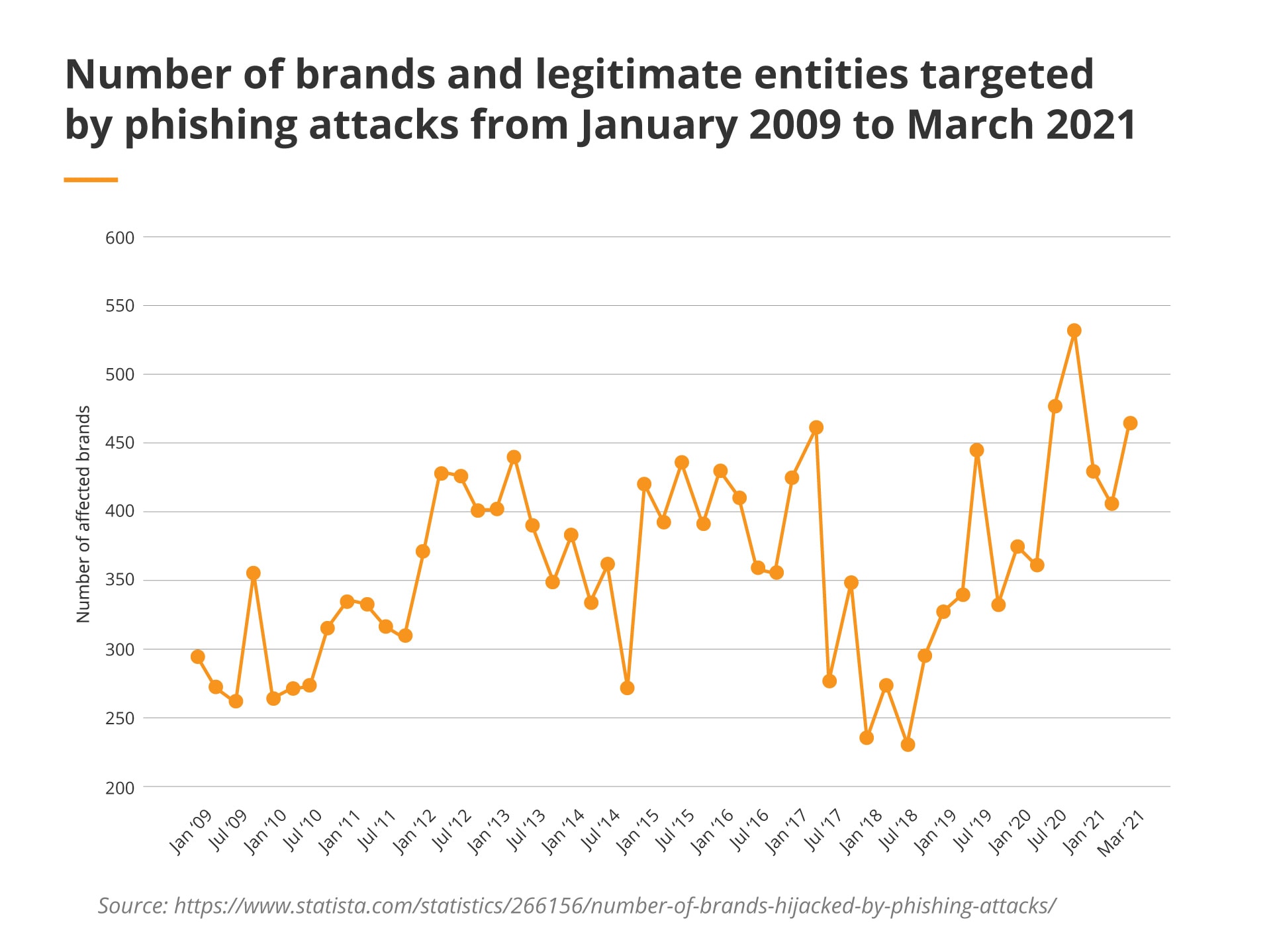
2021 is slowly coming to an end, so companies actively prepare different business areas for 2022. As cyberattacks are being launched every 39 seconds on average, the cybersecurity of organisations is one of the top priorities for now and the following years. Companies worldwide need a holistic approach and tech solutions that fit individual needs and include a complex business landscape (with remote work as an essential field to cover).
Due to the outburst of the COVID-19 pandemic, 2020 was the worst in terms of the number and sophistication of cyberattacks. Hackers worked extremely hard to take advantage of those tough times by committing such cyber crimes as:
- BEC attacks (Business Email Compromise attacks),
- ransomware attacks,
- mobile malware,
- cyberactivism,
- data breaches,
- phishing.
As Gartner predicts, by 2024, organisations adopting a cybersecurity mesh architecture will have reduced the financial impact of security incidents by an average of 90%. Before it happens, a lot has to be done to raise the business security level. Let’s focus on phishing and find out what companies can do to protect themselves in 2022.
What is phishing?
It is the practice of tricking Internet users (by means of deceptive email messages or websites) into disclosing personal or confidential information which can then be used illicitly. An American hacker first introduced the term in 1996 as an attempt to retrieve confidential information using email.
Beware of different types of phishing
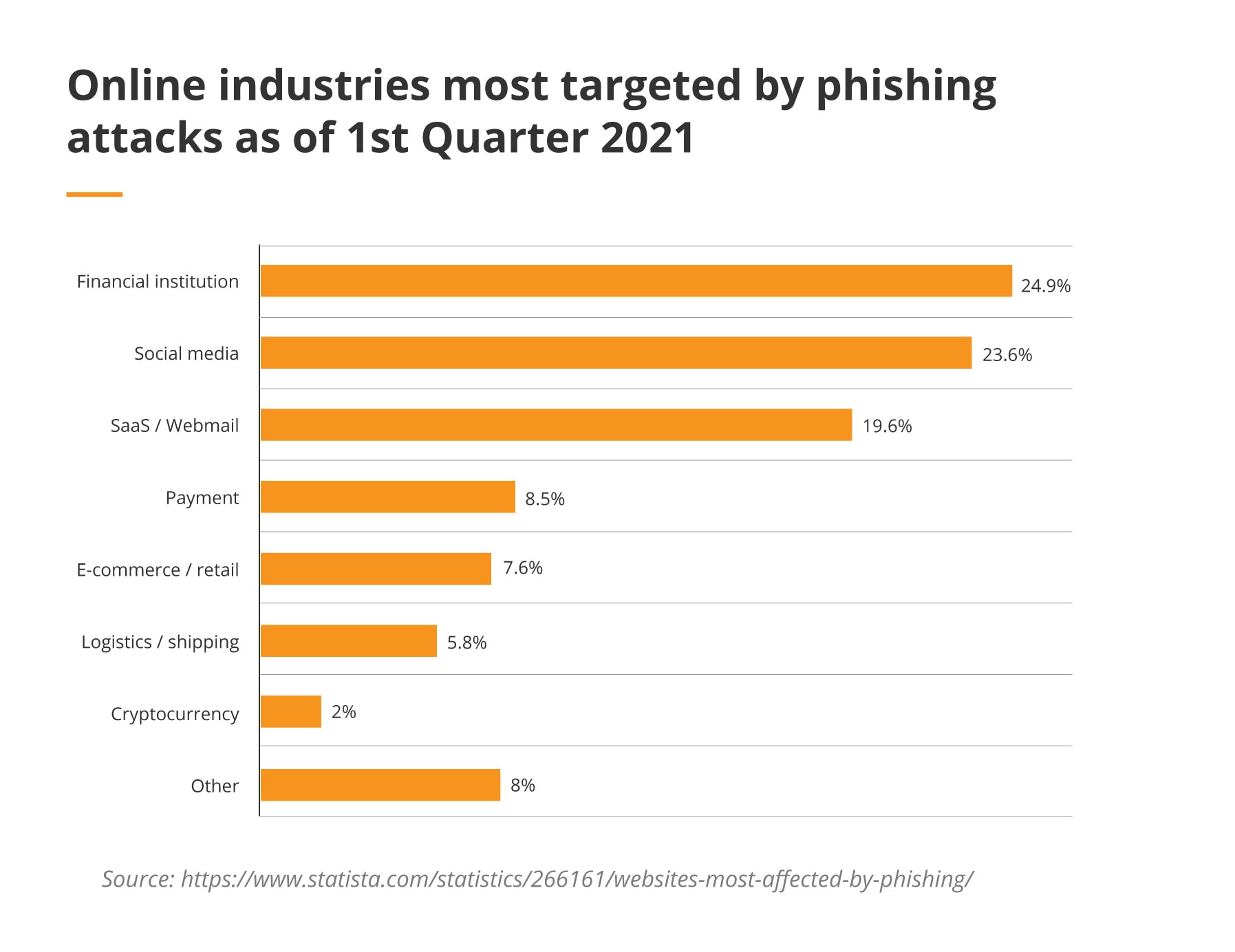
Phishing has more than one name. We need to be aware that hackers are busy inventing brand new ways of deceiving users and luring them into clicking a link, accessing certain apps, or sharing login information. There are a few different types of phishing attacks we need to pay attention to:
Spear phishing
These phishing attempts are directed at specific companies or individuals. What makes them different from standard phishing is that spear phishing attackers would frequently gather personal information about their target first and then use it to increase their chances of success. A famous example of a spear phishing attack is the case of Threat Group-4127 who targeted email accounts linked to Hillary Clinton’s 2016 presidential campaign. The group attacked more than 1,800 Google accounts implementing the accounts-google.com domain to threaten its targeted users.
Whaling
It is a type of spear phishing attack explicitly directed at senior-level executives and other high-profile persons. The email content will be drafted to reach a crucial managerial role in the company. It could contain an executive issue such as claiming to take legal action against the company or a serious client’s complaint.
Clone phishing
In a clone phishing attack, a legitimate and previously delivered email message containing an attachment or link would have its content and recipient’s address used to produce an almost identical message. In the new message, the attachment or link would be replaced with a malicious version and sent from an email address made to look like it comes from the original sender. To appear legitimate, the new message may say it is an updated version of the original. This technique of using social trust could be taken advantage of to access a new computer from a previously infected device.
SMiShing, ViShing and others
Phishing does not stop at emails. SMiShing is a type of attack which is done by SMS messages. SMS messages will ask you to call a specific number or visit a spoofed website to take action.
ViShing is another type of attack where you can receive a call from an automatic voice system to collect sensitive information. These attacks can be even more harmful than typical email scams, as the public awareness of this type of attack is still relatively low.
Tricky phishing tactics
Hackers search for potential victims’ weak points and use psychological tricks to lull them into a false sense of security. The best thing we can do is know hackers’ tactics to stay focused and double-check every suspicious email, link or push message. There are common tricks that should raise red flags to avoid falling into a trap:
A sense of urgency
Attackers try to make an impression of urgency, and the call-to-action is highlighted sometimes with an additional scare tactic of losing access to your account or money. It sounds like they care about your stuff more than you do: “Quick, take action to save what’s valuable for you!”
A “real” sender
The sender’s name looks like someone you know, but the email address has one or more characters changed. For example, suppose the address has the letter M (@freshmarket.com). In that case, attackers often send messages from another domain with the characters R and N (@freshrnarket.com), giving you the impression that the address is correct. Usually, it’s hard to detect it without going through the whole address letter by letter, but it’s worth checking.
Links in messages
Rolling over the links could show a different address than displayed. The address could also have a few characters changed, use similar-looking letters, e.g. with diacritics from other alphabets and/or lead to an unprotected website (HTTP instead of HTTPS). Double-checking the form of the link is also highly advised here.
Attachments and unusual files
Messages sometimes contain additional attachments. For example, if you used to get an invoice in a PDF document, but this time it came as a ZIP archive, it should raise your attention.
How can we avoid phishing?
Phishing has many names, and hackers’ tricks and scams are becoming more and more sophisticated with time. But as cybersecurity becomes one of the top priorities for companies, there are plenty of actions to take to make our businesses safer and scam-free. These are tailored tech solutions, employee education and knowledge sharing, and support of experienced cyber security specialists. They can help you create a cybersecurity plan that fits your business needs and threats.