USA: significant shifts in cybersecurity policy ahead
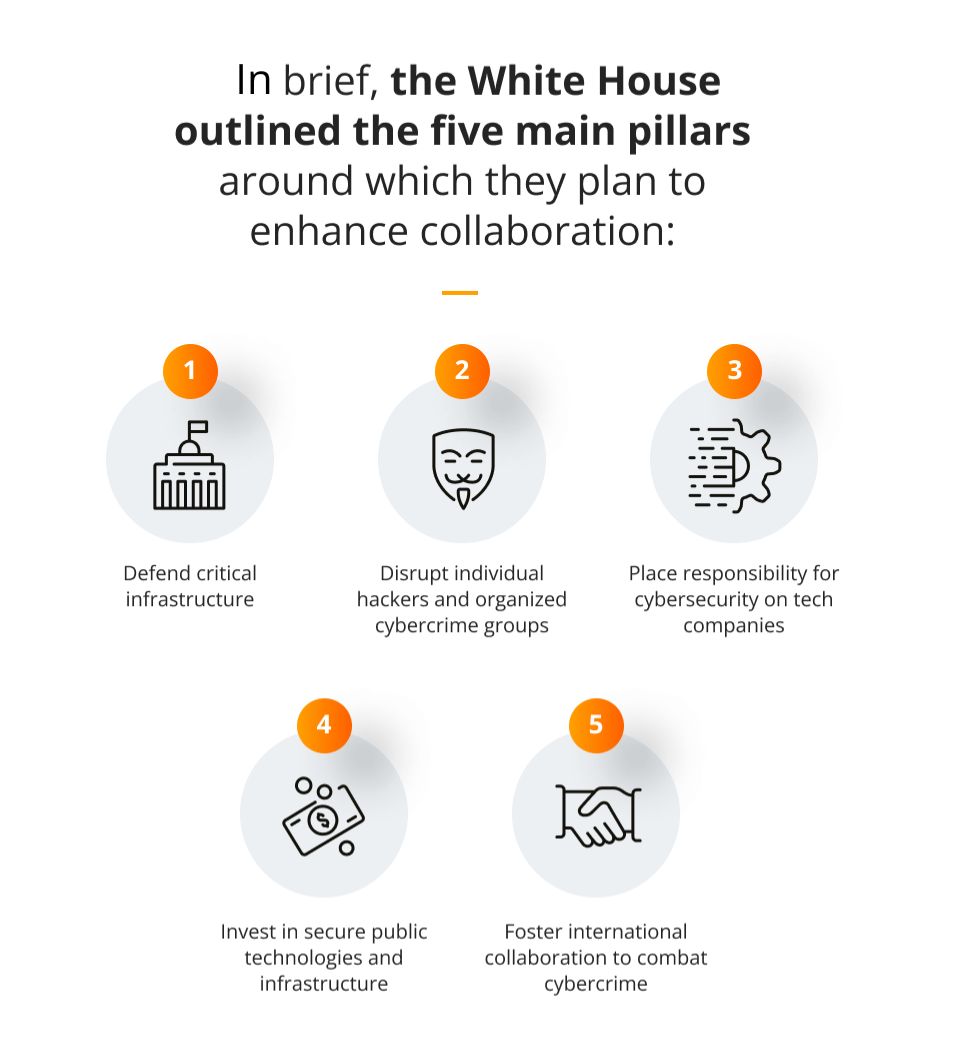
The Biden-Harris administration recently released the National Cybersecurity Strategy, which creates a new digital ecosystem in the U.S. that should be safe and secure for all Americans.
The National Cybersecurity Strategy replaces the old document issued by the Trump administration 5 years ago and aims to protect both national security and public safety as well as economic prosperity.
What we want to focus on today is point no. 3 – place responsibility for cybersecurity on tech companies, which pertains to all software companies operating in the American market.
Software companies to be responsible for security
What the new cybersecurity strategy emphasizes is the need for the private sector to take far greater responsibility for the software that they create — in order to assure that their systems are well-protected against cyber criminals. More responsibility will be demanded from larger and better-resourced organizations in particular — incorporating minimum security standards into their products will be a must.
This is a matter of both private and public security, since hackers are often backed by China, Russia or North Korea, and not letting them get into any critical networks is absolutely essential in terms of both politics and economics.
The most significant shift over decades
As of yet, the modus operandi has been quite different from what it is going to look like soon: right now, if there are any flaws or weaknesses within a security system, the client (whether this is a private person or business entity) currently assumes all of the risks.
They are responsible for not updating the software solutions that they use, and the creators cannot be punished for the mistakes that they made. In short, if you were unlucky and lost something — that’s too bad, c’est la vie — it’s your own fault though, so do better next time.
Now the U.S. government has decided to take a step back and ask why the system needed to be updated in the first place and what actually happened to make the software so vulnerable. Maybe the minimum required standards weren’t met…? Maybe the makers of the software unnecessarily jeopardized their clients’ safety due to carelessness or oversight?
The responsibility for software security is therefore to be transferred to those who actually created the software, and not to those who use it. In other words, the most vulnerable party will be better protected, and the most powerful — finally liable for their actions (or lack of actions, to be more precise).
The end of the ‘optional’ era, without any real obligations
For years, companies have been told that they can voluntarily report hacking attempts and intrusions, but it hasn’t been required of them. Also, they have been allowed to simply patch their systems in order to fix detected vulnerabilities. However, as Anne Neuberger, the deputy national security adviser for cyber and emerging technologies, has said:
The fundamental recognition in the strategy is that a voluntary approach to securing [critical infrastructure and networks] is inadequate.Anne Neubergerthe deputy national security adviser for cyber and emerging technologies
This shift in attitude is quite significant, and also necessary in order to make the entire ecosystem both easier to defend and much more resilient against any cyber threats. And this is also consistent with the political narrative of the EU and Australia — the western world seems to be pretty unanimous in their efforts to ensure digital safety. But this comes as no surprise, since these days, this translates directly into national and international security, and from the lowest to the highest levels.
Possible consequences
Of course, one of the most important aspects of this shift is the penalties that could be imposed on the companies that don’t comply. As far as we know, the disciplinary mechanisms from GDPR or NIS2 are going to be put in place, meaning that organizations will have to pay high fines for not meeting the minimum standards of security and endangering their clients. Should they be worried? Not at all — as long as they take a good approach and follow proper security measures.
How to prepare
If you’re a software development company, you should be interested in complying with the newest regulations, whether you operate in the American market or not. As we’ve mentioned above — soon it is going to look more or less the same in the EU and the UK, as well as in Australia. There’s no escaping the changes that are about to happen, but you can prepare your business and avoid any major disruptions.
Here’s what you can do:
1. Hire a cybersecurity expert or experts.
You may decide to expand your internal team with some new members — responsible solely for cybersecurity. Keeping everything in-house may be a good idea for smaller companies with less complex infrastructure.
2. Cooperate with an experienced IT partner.
If you’re a medium-sized or larger organization — you may want to build your security strategy together with an experienced partner, in order to off-load your internal resources and operate even more effectively. For example, security management during software development (Security Development Lifecycle) is one of our core services, meaning, we’ve already been doing what everyone else will soon be forced to do for quite some time.
This means that cooperating with Future Processing would give you a more thorough competitive edge from the ground up, since you would benefit from all of the invaluable experience that others are just about to start gaining.
No matter which route you choose to take, take it seriously, but also try not to panic. With a little bit of expert help (from internal or external sources), your business activities won’t be disrupted, and you will be able to get through more challenging times with ease.