What is cyber resilience and what are the benefits?
In the world of constantly growing cyber threats, cyber resilience is one of the hottest topics - especially in the wake of the Cyber Resilience Act EU proposal. Let's look at what cyber resilience is and how to achieve it.
Cyber resilience: what it is and why it matters
Cyber resilience encompasses a set of proactive cybersecurity strategies, practices, and technologies aimed at minimising the impact of adverse cyber events and ensuring business continuity in the face of disruptions.
In today’s interconnected and technology driven world, security incidents are a major concern for organisations of all sizes and across all industries. These threats come in various forms, such as data breaches, ransomware attacks, network outages, or even natural disasters that affect digital infrastructure. The consequences of these incidents can be severe, leading to financial losses, reputational damage, legal liabilities, and compromised customer data.
These are the reasons why cybersecurity and cyber resilience really matter. They ensure business continuity allowing organisations to continue their operations and deliver critical services even in the face of a cyber attack or disruption. They ensure protection of sensitive data and critical infrastructure, enhance the organisation’s reputation and trust and help meeting regulatory requirements. They also give a great advantage when it comes to cost savings and adaption to changing threat landscape.
Cyber Resilience Act – an EU legislative proposal
The Cyber Resilience Act (CRA) is an EU legislative proposal listing standard cybersecurity requirements for IT solutions, digital products, and software. The goal is to make them more secure and reliable. CRA also defines the guiding principles for developing these types of products, with the entire product lifecycle in mind.
Head to my recent post about Cyber Resilience Act – I am writing about its aims, key components, reasons why it is crucial for every software development company to plan the actions regarding CRA, and more.
Cyber threats and the key components of cyber resilience strategy
Cyber threats are malicious activities or attacks that exploit vulnerabilities in computer systems, network or digital infrastructure. They can have a wide range of objectives, including unauthorised access to sensitive information, disruption of services and business operations, financial gain or sabotage.
To effectively counter these threats, organisations need to develop a comprehensive cyber resilience strategy and security posture that encompass several components.
The main components of cyber resilience are:
- risk assessment and management, which help identify vulnerabilities and threats and their potential impact on the organisation and its business processes.
- robust cybersecurity measures such as firewalls, intrusion detection systems, antivirus software, secure network configurations, encryption and regular security updates that protect systems and improve cyber resilience.
- incident response planning, including clear guidelines on how to respond, who to contact, and what are the steps to take during and after an incident to protect business operations.
- business continuity and disaster recovery plans including maintaining backups of data, establishing redundant systems and regular testing of the recovery procedures that increase cyber resilience.
- employee education and awareness which help reduce the likelihood of human error leading to a successful cyber attack.
- collaboration and information sharing which allows for the exchange of threat intelligence best practises and lessons learned, leading to a better cyber resiliency.
- continuous monitoring and assessment allowing organisations to detect and respond to potential threats in real-time and identify vulnerabilities to ensure the cyber resilience strategy and security solutions remain effective.
- regular updates and patch management, critical to mitigate vulnerabilities that may be exploited by cybercriminals.
- third party risk management allowing to assess and manage cybersecurity risks associated with third-party vendors or partners.
- governance and leadership meaning the senior management should actively support and promote a culture of cybersecurity and cyber resilience throughout the organisation.
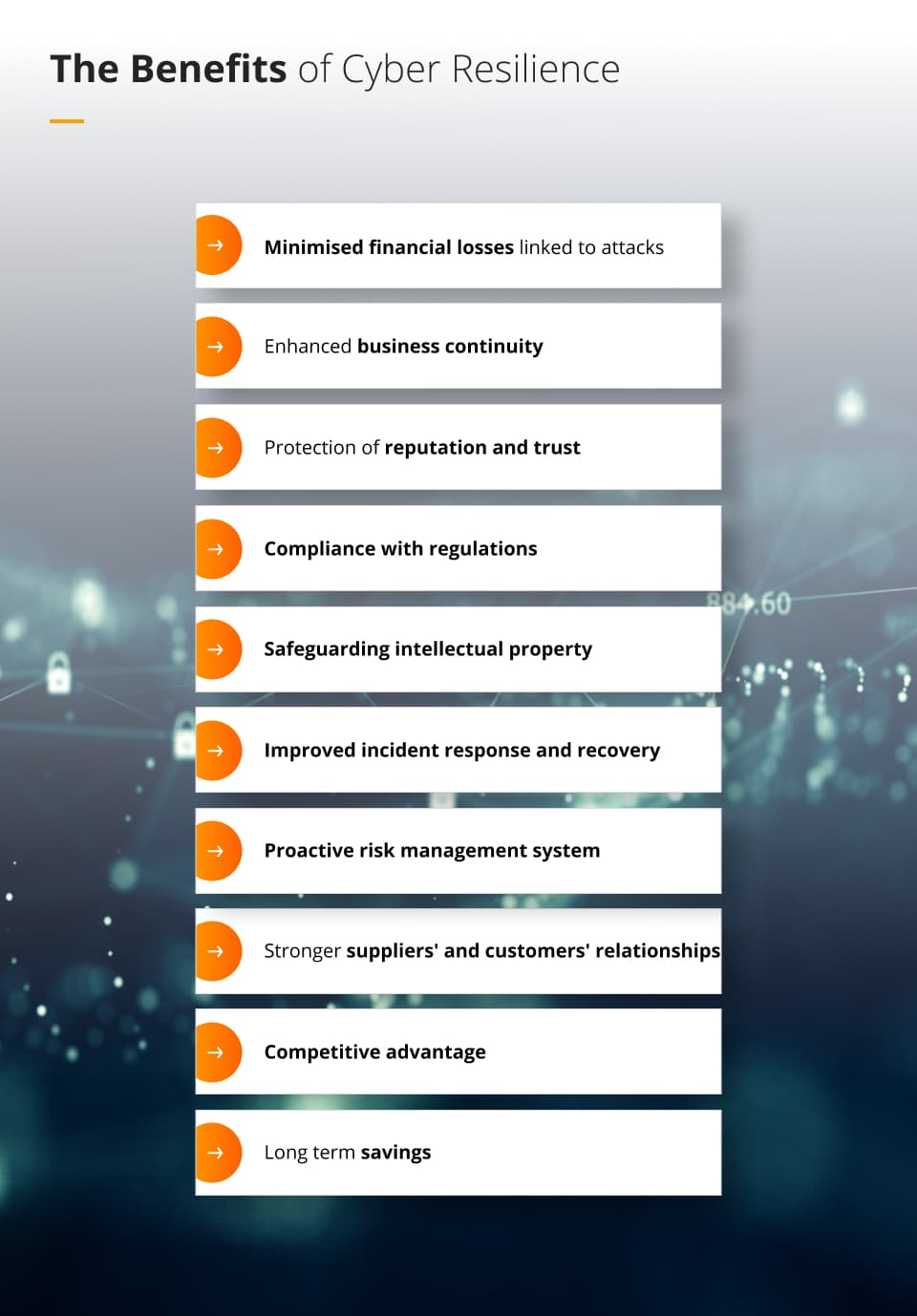
The benefits of cyber resilience
Cyber resilience offers numerous benefits, including:
Minimised financial losses linked to attacks
Cyber attacks may be expensive due to the costs associated with incidents response, recovery and remediation. Being cyber resilient means organisations can minimise the financial impact of attacks by implementing preventive measures, having effective incident response plans and reducing downtime.
Enhanced business continuity
Cyber resilience ensures the organisations can maintain essential operations and services even in the face of cyber incidents or disruptions. By implementing robust cybersecurity measures and having disaster recovery plans in place, organisations can minimise downtime, increase customers’ trust and avoid significant business interruptions.
Protection of reputation and trust
A cyber attack can severely damage an organisation’s reputation and erode customer trust. By investing in cyber resilience, organisations demonstrate their commitment to safeguarding sensitive information and maintaining the confidentiality and availability of critical data.
Compliance with regulations
More and more industries become subject to strict data protection and privacy regulations, such as the aforementioned Cyber Resilience Act. Implementing a cyber resilience strategy helps organisations meet these regulatory requirements, ensuring the protections of customer data, avoiding legal penalties and maintaining compliance with ever evolving cybersecurity laws and regulations while fulfilling its mission or business objectives.
Safeguarding intellectual property
Cyber attacks aimed at stealing or compromising intellectual property can have several consequences. Cyber resilience measures protect against unauthorised access, theft, or manipulation of intellectual property, ensuing that organisations can continue to innovate and maintain their competitive edge.
Improved incident response and recovery
By having well-defined processes, clear roles and responsibilities, and effective incident response plans in place, organisations can respond promptly to cyber incidents, mitigate their impact and respond and recover critical systems and data more efficiently.
Proactive risk management system
By identifying and assessing potential vulnerabilities, organisations can mitigate risks before they can be exploited by bad actors. Such a proactive approach helps reduce the likelihood and impact of successful attacks or a security breach.
Stronger suppliers’ and customers’ relationships
Organisations that prioritise cybersecurity demonstrate their commitment to protecting shared data and information which can enhance trust and foster stronger partnerships.
Competitive advantage
Organisations that demonstrate a strong cyber resilience posture are often viewed as more trustworthy by customers, partners and investors, giving them a competitive advantage.
Long-term savings
While investing in cyber resilience may mean some extra costs, it will lead to long-term cost saving by minimising the likelihood and disruptive impact of future incidents.
How to achieve cyber resilience?
Achieving cyber resilience requires a comprehensive and proactive approach. Here are key steps that need to be taken in the process:
- assess risk by conducting a thorough risk assessment, while understanding the specific risks your organisation faces, based on its industry, size and other characteristics;
- develop a cybersecurity strategy that aligns with business objectives and addresses identified risks;
- implement layered security controls to create a strong defence-in-depth approach;
- establish strong access controls to ensure only authorised individuals can access sensitive data, systems and resources;
- educate and train employees on regular basis, fostering a culture of cybersecurity awareness and cyber resilience throughout your organisation;
- develop an incident response plan with clear roles, responsibilities and communication channels;
- regularly test and update systems;
- have regular backup and recovery plans which will help in the event of data loss or ransomware attacks;
- utilise SIEM (security information and event management) solutions to consolidate and analyse security logs for early threat detection;
- collaborate and share threat intelligence; stay informed of the latest and emerging threats.
In today’s digital world, cyber resilience is essential. By prioritising it, organisations can better safeguard their operations, customers, and overall business interests in the face of an increasingly complex and challenging cyber landscape and an ever increasing number of security risks. Times when cyber resiliency was a “nice-to-have” are long gone – today, cyber resilience is one of the most critical aspects of every business. It should be prioritised and taken extremely seriously.
At Future Processing, we excel at equipping our clients with the best security solutions. Get in touch today to speak to me or one of our specialists – we are happy to support and improve your cyber resilience and overall cybersecurity posture.