The human factor in cybersecurity: the greatest challenge. Part I
Do you know what your greatest challenge is when it comes to the cybersecurity of your organisation? It's your employees and colleagues. In this article – the first of two speaking about the human factor in cybersecurity, I am discussing the role of human element in cybersecurity.
The human factor in cybersecurity: the role of human element in cybersecurity
You can take care of all cybersecurity aspects of your organisation you can think of, but at the end of the day what can cost you dearly is not a software that failed, but a mistake done by your employee.
Statistics say that in the last year 94% of organisations have experienced insider data breaches, with human error being the top cause of serious incidents, according to 84% of IT leaders surveyed. To understand the reasons, it’s enough to look at other statistics: 50% of respondents admitted to allowing family or friends to use their work-issued devices, while 58% of organisations report that employees ignore their cybersecurity guidelines.
The significant role that individuals play in the overall security of digital systems, networks, and information is called the human factor. While technological advancements and sophisticated security measures are crucial in safeguarding against cyber threats, humans remain a critical element in both the success and vulnerability of these systems. Understanding and managing the human element is essential for achieving robust cybersecurity.
Addressing the problem: human risks that influence cybersecurity
Some of the best strategies that organisations can adopt to address the problem of human risks include cybersecurity training and awareness, strong password policies, employee monitoring and limiting access privileges – below we will look at them in more detail.
It’s important to remember that addressing the human factor in cybersecurity requires a holistic approach that involves not only technology but also people, processes, and culture. By investing in education, training, and creating a security-conscious environment, organisations can significantly reduce the impact of human-related vulnerabilities and cybersecurity risks and enhance their overall cybersecurity posture.
How does human error relate to security risks?
As shown by the statistics, human error is one of the most significant contributors to security risks in the cybersecurity landscape. It refers to mistakes or oversights made by individuals that lead to vulnerabilities or security breaches within an organisation’s digital systems, networks, or data. Understanding how human error relates to security risks is crucial for implementing effective measures to prevent and mitigate a potential security incident.
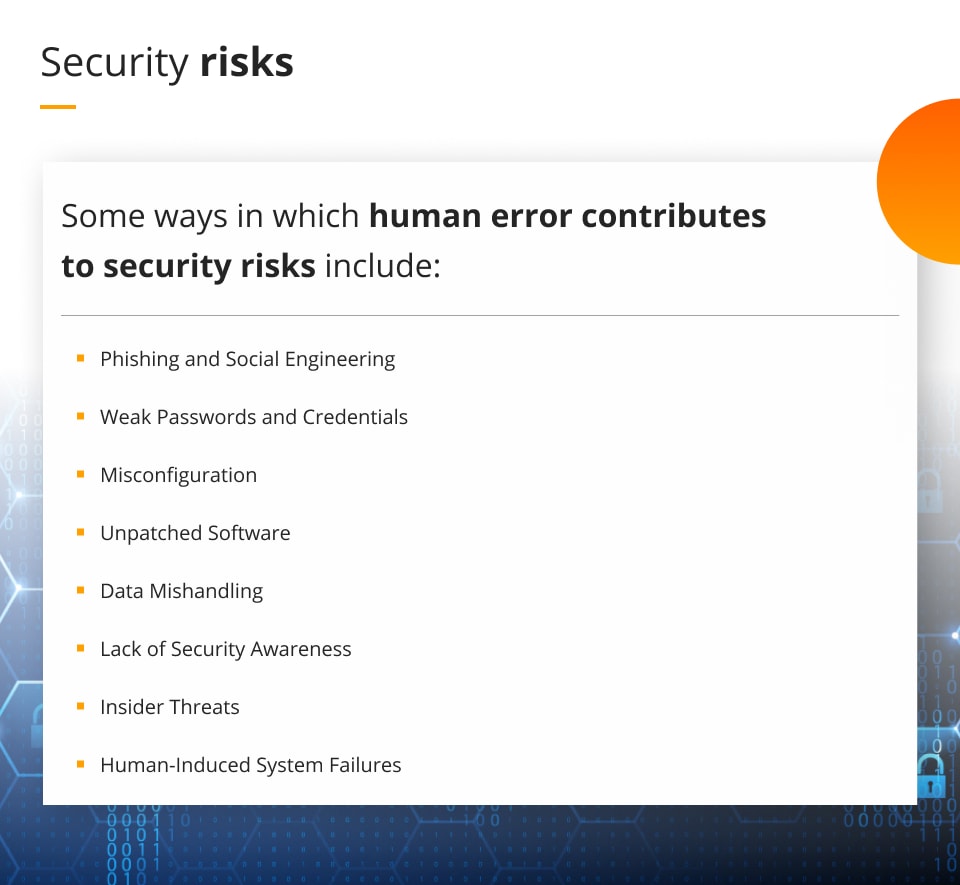
Some ways in which it contributes to security risks include:
Phishing and Social Engineering:
Phishing attacks rely heavily on employee behaviour. Cybercriminals send deceptive emails or messages that appear legitimate, tricking users into clicking on malicious links, downloading malware, or revealing sensitive information. Human error, such as not being vigilant about checking email sources or blindly following instructions, can lead to falling victim to these scams.
Weak Passwords and Credentials
Many security breaches occur due to weak passwords or credentials. Employees might use easily guessable passwords, reuse passwords across multiple accounts, or share login credentials, making it easier for attackers to gain unauthorised access to systems.
Misconfiguration
Configuring security settings incorrectly can lead to vulnerabilities. Misconfigured firewalls, cloud services, or network devices might inadvertently expose critical data or services to unauthorised users.
Unpatched Software
Failure to apply timely security patches and updates is another form of human error that exposes systems to known vulnerabilities. Outdated software can be exploited by cybercriminals to gain access to a network or compromise sensitive data.
Data Mishandling
Human errors related to data handling can lead to significant security risks. For example, sending sensitive information to the wrong recipients, leaving sensitive documents unsecured, or improperly disposing of confidential data can all result in data breaches.
Lack of Security Awareness
Employees who are not adequately trained or aware of cybersecurity best practices are more likely to make mistakes that compromise security. They may not recognise potential threats or may not know how to respond appropriately to security incidents.
Insider Threats
Insider threats happen when employees intentionally or unintentionally pose a risk to the organisation’s security. For instance, an employee might accidentally download malware or unknowingly share sensitive data with unauthorised individuals.
Human-Induced System Failures
In complex IT environments, human factors can cause system failures or downtime that expose the organisation to potential attacks or data loss.
Psychological manipulation in cybersecurity: an overview of phishing attacks
Psychological manipulation is a key tactic used in cybersecurity, especially in phishing attacks. Phishing is a type of social engineering attack where cybercriminals use deceptive tactics to trick individuals into revealing sensitive information, such as login credentials, financial data, or personal details.
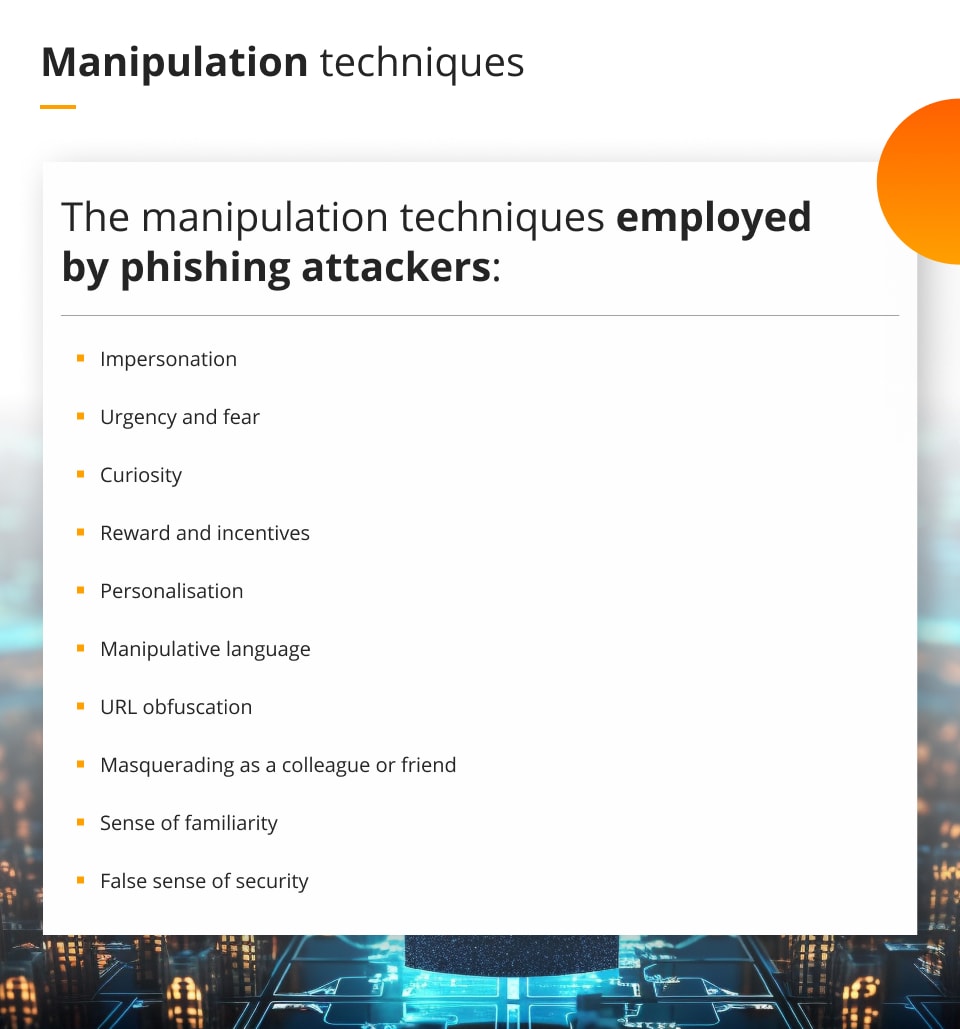
These attacks exploit human psychology and emotions to increase the chances of success. Here’s an overview of phishing attacks and the psychological manipulation techniques they employ:
- Impersonation: phishing emails often impersonate legitimate entities, such as banks, government agencies, or well-known companies. The attackers use familiar branding, logos, and email addresses to make the message appear authentic, instilling trust in the recipient.
- Urgency and fear: phishing emails often create a sense of urgency or fear to prompt immediate action from the recipient. For example, they may claim that the recipient’s account will be suspended, or there is a security breach that requires immediate attention.
- Curiosity: attackers may craft emails that pique the recipient’s curiosity, enticing them to click on a link or open an attachment to learn more. This technique leverages the natural human tendency to seek new information.
- Reward and incentives: phishing emails may promise rewards, discounts, or exclusive offers to lure recipients into clicking on malicious links or providing sensitive information.
- Personalisation: phishing emails might include personal information obtained from data breaches or social media profiles to make the messages appear more legitimate and increase the chances of success.
- Manipulative language: phishing emails often use persuasive and manipulative language to create a sense of trust and credibility. They may use emotional appeals, flattery, or empathy to manipulate the recipient’s emotions.
- URL obfuscation: attackers often hide malicious URLs behind hyperlinked text that appears legitimate. Hovering over the link may not reveal the true destination, leading recipients to click on dangerous links unwittingly.
- Masquerading as a colleague or friend: in targeted attacks known as “spear phishing,” attackers impersonate someone known to the recipient, such as a colleague, friend, or family member, to lower the recipient’s guard and increase the likelihood of success.
- Sense of familiarity: phishing emails may reference recent events or ongoing projects within the recipient’s organisation to create a sense of familiarity and credibility.
- False sense of security: attackers may include statements claiming that the email is secure or has been scanned for viruses to deceive recipients into thinking the email is safe.
To protect against phishing attacks and psychological manipulation, individuals and organisations should be cautious about clicking on links or opening attachments in unsolicited emails, verify the sender’s email address and the legitimacy of the message before taking any action, use multi-factor authentication whenever possible to add an extra layer of security, regularly update and patch software to protect against known vulnerabilities and educate employees and stakeholders about phishing and cybersecurity best practices through training and awareness programs.
By understanding the psychological tactics employed in phishing attacks and promoting cybersecurity awareness, individuals and organisations can better defend against these threats and protect their sensitive information.
Stay tuned – the next article will further expand this broad topic. I will present some key strategies for improving employee cybersecurity awareness, and more.