Security architecture 101: understanding the basics
How important is security architecture for every organisation? If effective, it can save a lot of money. If inexistent, it will surely mean trouble.
According to Cybersecurity Ventures, in 2023 the cost of cybercrime will hit $8 trillion and by 2025 it will grow to $10.5 trillion. On the other hand – as reported by HackerOne 2022 – in 2022 ethical hackers discovered over 65,000 vulnerabilities, up by 21% over 2021.
Key components of security architecture: security principles
Some key components of security architecture and associated security principles include:
Confidentiality
Confidentiality focuses on ensuring that sensitive information is accessible only to authorised individuals. Key security components for confidentiality include encryption, access controls, data classification, and secure communication channels.
Integrity
Integrity ensures that data remains accurate, complete, and unaltered throughout its lifecycle. Security measures such as data validation, checksums, digital signatures, and audit trails help maintain data integrity and prevent unauthorised modifications or tampering.
Availability
Availability ensures that systems and resources are accessible and usable when needed. It involves implementing measures to prevent disruptions, downtime, or denial of service attacks. Redundancy, fault tolerance, disaster recovery plans, and robust network infrastructure are essential components of ensuring availability.
Authentication
Authentication verifies the identity of users or entities attempting to access resources or systems. Security components for authentication include strong passwords, multi-factor authentication (MFA), biometrics, and secure authentication protocols like OAuth or SAML.
Authorisation
Authorisation determines the permissions and privileges granted to authenticated users or entities. It involves defining access controls, role-based access control (RBAC), and least privilege principles. Authorisation mechanisms ensure that users have appropriate access rights based on their roles and responsibilities.
Auditing and Logging
Auditing and logging are critical for monitoring and detecting security incidents, as well as for compliance and forensic purposes. Security architecture should include robust logging mechanisms, intrusion detection systems (IDS), security information and event management (SIEM) tools, and regular security audits.
Network Security
Network security components protect data in transit and secure network infrastructure. These include firewalls, intrusion prevention systems (IPS), virtual private networks (VPNs), network segmentation, and secure protocols such as SSL/TLS.
Application Security
Application security focuses on securing software and applications throughout the development and deployment lifecycle. Components of application security include secure coding practices, vulnerability assessments, penetration testing, input validation, and web application firewalls (WAFs).
Incident Response
Incident response involves a predefined plan and procedures for handling and mitigating security incidents. It includes components such as incident detection systems, incident response teams, incident response plans, and regular testing and drills.
Security Governance
Security governance establishes the framework, policies, and procedures for managing security within an organisation. It includes defining roles and responsibilities, establishing security standards, conducting risk assessments, and ensuring compliance with applicable laws and regulations.
These security principles and components form the basis for designing and implementing a comprehensive security architecture. Organisations should consider them when developing their security strategy and architecture to protect their critical assets, mitigate risks, and maintain the confidentiality, integrity, and availability of their systems and data.
Security frameworks: TOGAF, SABSA, OSA
Structured methodologies or sets of guidelines designed to help organisations establish and maintain effective security practices are called security frameworks. These frameworks provide a systematic approach to identify, assess, and manage security risks, as well as to implement and monitor security controls. They often encompass a wide range of security domains, including information security, cybersecurity, physical security, and operational security.
Here is an overview of some well-known security frameworks used in the field of security and enterprise architecture:
TOGAF (The Open Group Architecture Framework)
TOGAF is a widely adopted framework for enterprise architecture that provides a structured approach to designing, planning, implementing, and governing an organisation’s IT architecture. While TOGAF does not focus solely on security, it incorporates security considerations throughout the architecture development process.
TOGAF provides guidance on incorporating security requirements, risk management, and compliance into the overall architecture. It helps organisations align their security objectives with their business goals and ensures security is an integral part of the enterprise architecture.
SABSA (Sherwood Applied Business Security Architecture)
SABSA is a framework specifically designed to address security architecture and risk management. It provides a holistic approach to integrating security into the overall enterprise architecture. SABSA emphasises the alignment of security objectives with business goals, risk management, and governance.
It focuses on establishing a business-driven and risk-based security architecture that covers strategic, operational, and technology aspects. SABSA provides a structured methodology for identifying security requirements, designing security solutions, and implementing security controls.
OSA (Open Security Architecture)
OSA is an open-source security architecture framework that provides a structured approach to designing and implementing security solutions. OSA offers a set of architectural patterns, reference models, and best practices to address common security challenges.
It covers various domains of security, including network security, application security, identity and access management, and security governance. OSA helps organisations adopt a modular and reusable approach to security architecture, allowing for flexibility and customisation based on specific requirements.
Other frameworks which can be used include NIST Cybersecurity Framework, ISO 27001, PCI-DSS, HIPAA, SOC 2, and Zero Trust Security Principles. The choice of framework depends on the organisation’s specific needs, objectives, and existing architectural practices. Organisations may adopt one or a combination of these frameworks to guide their security architecture efforts and ensure a comprehensive and integrated approach to security within their enterprise architecture.
Cloud security architecture
Cloud security architecture refers to the design and implementation of security measures and controls within a cloud computing environment. It involves the use of various technologies, processes, and best practices to protect data, applications, and infrastructure deployed in the cloud, with the end goal to ensure the confidentiality, integrity, and availability of cloud resources while mitigating risks and complying with relevant regulations.
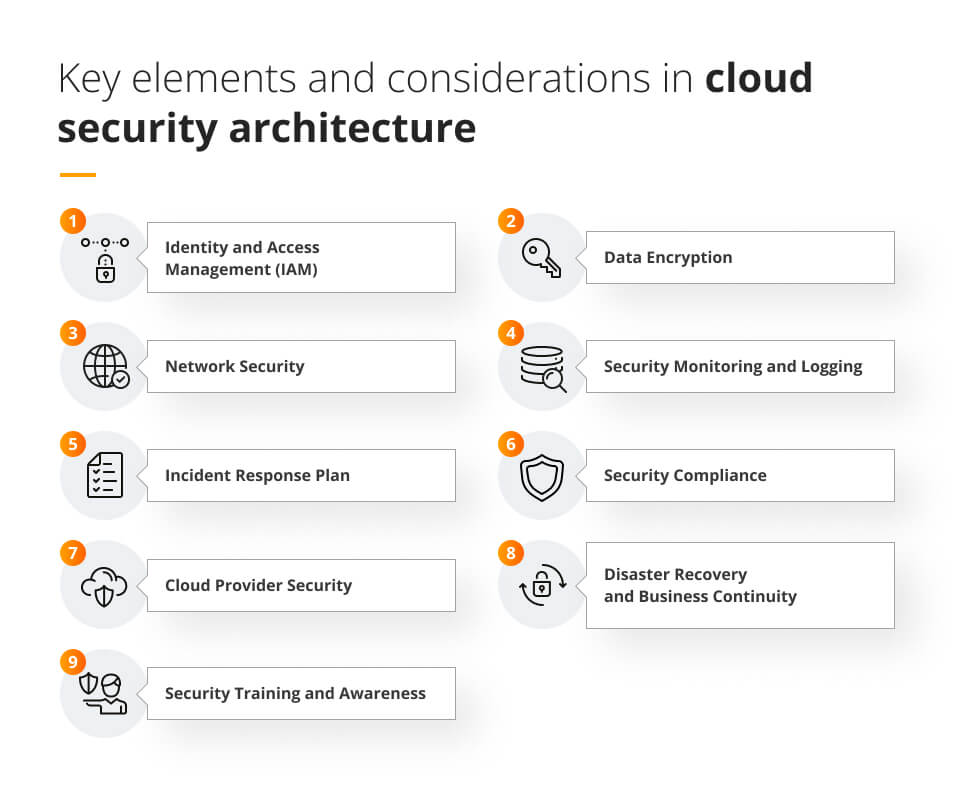
Key elements and considerations in cloud security architecture include:
- Identity and Access Management (IAM), such as multi-factor authentication and fine-grained access controls, necessary to manage user identities and permissions within the cloud environment.
- Data Encryption, needed to protect sensitive data both in transit and at rest. It includes encrypting data stored in cloud storage services and encrypting communication channels between cloud components.
- Network Security to isolate resources, control traffic flow, and prevent unauthorised access.
- Security Monitoring and Logging to track and analyse activities within the cloud environment.
- Incident Response Plan that outlines the steps to be taken in the event of a security breach or incident. This includes procedures for containment, investigation, mitigation, and recovery.
- Security Compliance, ensuring compliance with relevant regulations and industry standards, such as GDPR, HIPAA, or PCI DSS, based on the specific requirements of your organisation and the data you handle in the cloud.
- Cloud Provider Security, ensuring that the provider offers robust security measures.
- Disaster Recovery and Business Continuity that include regular data backups, replication, and redundant systems to ensure business continuity in case of a cloud service outage or data loss.
- Security Training and Awareness to help educate and train employees on cloud security best practices, including safe data handling, secure password management, and recognising social engineering and phishing attacks.
Cloud security architecture should always be tailored to the specific requirements and risk profile of each organisation. To ensure ongoing protection, it should be regularly reviewed and updated.
Business security architecture
Business security architecture refers to the design and implementation of security controls and practices within an organisation to protect its assets, operations, and stakeholders from various threats and risks. It involves aligning security measures with the overall business objectives and requirements, as well as ensuring compliance with relevant regulations and industry standards.
Some key elements and considerations in business security architecture include:
- Risk Assessment and Management to identify potential threats and vulnerabilities that could impact the organisation.
- Security Policies and Procedures that outline the organisation’s expectations, guidelines, and best practices for security. This includes policies for data classification, acceptable use of assets, incident response, and employee security awareness.
- Asset Protection, which may include access controls, encryption, physical security controls, and data loss prevention mechanisms.
- Network and Infrastructure Security, including firewalls, intrusion detection and prevention systems, secure remote access, and network segmentation.
- Application Security to ensure that applications developed and used within the organisation follow secure coding practices and undergo regular security testing and code reviews.
- Security Awareness and Training, needed to educate employees about security risks, best practices, and their responsibilities in maintaining a secure environment.
- Incident Response and Business Continuity that outlines the steps to be taken in case of security incidents, including incident detection, containment, investigation, and recovery.
- Compliance and Regulatory Requirements.
- Security Governance and Oversight to oversee and manage the organisation’s security efforts. This may involve creating a security team or committee, defining roles and responsibilities, conducting periodic security audits, and ensuring compliance with internal policies and external requirements.
Business security architecture should be an ongoing and iterative process, continuously adapting to evolving threats and organisational changes. It requires collaboration between business stakeholders, IT teams, and security professionals to ensure that security measures align with business goals while effectively protecting the company’s assets and operations.
Benefits of robust security architecture
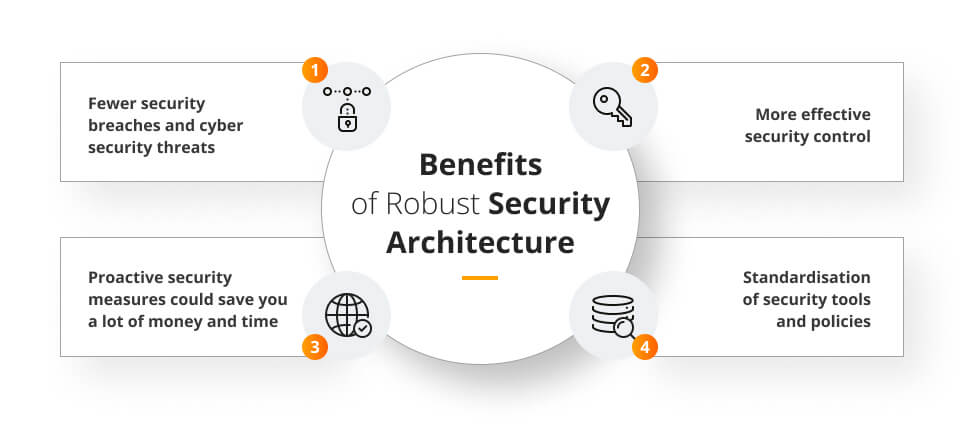
Robust security architecture provides numerous benefits to organisations and helps them stay secure in the world of ever changing security threats. The key advantages of effective security architectures include:
Fewer security breaches and cyber security threats
A well-designed security architecture helps protect critical assets, including sensitive data, intellectual property, customer information, and physical resources. It establishes controls and safeguards to prevent unauthorised access and minimise data breaches and cyber security threats, saving a lot of money, effort and reputation.
Proactive security measures could save you a lot of money and time
Proactive security architecture saves organisations both time and money by preventing incidents, minimising downtime, reducing incident response costs, avoiding legal penalties, protecting brand reputation, optimising resource allocation, and enabling competitive advantage. Investing in proactive security measures is a strategic decision that yields long-term cost savings and business benefits.
More effective security control
A well-designed security architecture enables organisations to implement more effective security controls, leading to comprehensive protection, risk reduction, centralised management, customisation, integration, scalability, compliance, improved incident response, and continuous improvement. These benefits collectively contribute to a stronger security posture and better protection of organisational assets and operations.
Standardisation of security tools and policies
Standardisation of security tools and policies through a security architecture brings benefits such as a consistent security posture, ease of deployment and management, interoperability, cost efficiency, simplified training, compliance readiness, streamlined incident response, and enhanced collaboration.
Best practices for effective security architecture: tips and strategies
Some best practices, tips and strategies to ensure an effective security architecture include:
1. Understanding the Business
Gain a deep understanding of the organisation’s business objectives, operations, and critical assets. Align the security architecture with the specific needs, risks, and compliance requirements of the organisation to ensure that security measures are relevant and effective.
2. Taking a Risk-Based Approach
Conduct a comprehensive risk assessment to identify and prioritise security risks. This helps in focusing resources and efforts on addressing the most critical risks. Implement controls and safeguards that are proportional to the identified risks to optimise the use of resources.
3. Following Security Frameworks and Standards
Leverage established security frameworks, such as the NIST Cybersecurity Framework, ISO 27001, or CIS Controls. These frameworks provide guidance on best practices, controls, and processes for designing and implementing effective security architectures. Aligning with recognised standards helps ensure comprehensive coverage and compliance.
4. Adopting a Layered Defense Strategy
Implement a layered security approach that incorporates multiple defense mechanisms at different levels, including network, system, application, and data. This defense-in-depth strategy minimises the chances of a single point of failure and provides overlapping protection.
5. Implementing Strong Identity and Access Management (IAM)
Establish robust IAM controls to manage user identities, authentication, authorisation, and access permissions. Implement multi-factor authentication, least privilege principles, and regular access reviews to ensure appropriate access controls and minimise the risk of unauthorised access.
6. Employing Defense-in-Depth for Perimeter Security
Utilise multiple layers of security controls at the network perimeter, such as firewalls, intrusion detection/prevention systems, and secure web gateways. This helps in detecting and preventing unauthorised access, network attacks, and malicious activities.
7. Securing Application Development
Incorporate secure coding practices throughout the software development lifecycle. Conduct regular security code reviews, vulnerability assessments, and penetration testing to identify and remediate application vulnerabilities. Implement application-level security controls, such as secure authentication, input validation, and output encoding.
8. Encrypting Sensitive Data
Employ encryption techniques to protect sensitive data both in transit and at rest. Use strong encryption algorithms and secure key management practices to safeguard data confidentiality and integrity.
9. Establishing Monitoring and Logging
Implement a robust security monitoring and logging system to detect and respond to security incidents. Utilise Security Information and Event Management (SIEM) tools to centralise log data, analyse security events, and generate actionable alerts for incident response.
10. Regularly Updating and Patching of Systems
Maintain a disciplined patch management process to ensure that operating systems, applications, and security tools are up to date with the latest patches and security updates. This helps mitigate known vulnerabilities and reduce the risk of exploitation.
11. Conducting Security Awareness and Training
Foster a security-conscious culture by providing regular security awareness training to employees. Educate them about common threats, social engineering, and safe computing practices. Encourage reporting of security incidents and provide channels for reporting potential security concerns.
12. Performing Regular Security Assessments and Audits
Conduct periodic security assessments, vulnerability scans, and penetration testing to identify weaknesses and areas for improvement. Perform internal and external audits to evaluate the effectiveness of security controls and ensure compliance with regulatory requirements.
13. Staying Informed and Adapting
Stay up to date with the latest security threats, trends, and emerging technologies. Continuously monitor the threat landscape and adjust security measures accordingly. Engage with industry forums, security communities, and professional networks to stay informed and share knowledge.
14. Engaging Stakeholders and Obtaining Buy-in
Collaborate with business stakeholders, IT teams, and executive leadership to ensure their involvement and support for the security architecture. Clearly communicate the benefits and importance of security measures to obtain buy-in and establish a security-focused organisational culture.
15. Continuously Improving and Evolving
Security architecture should be treated as an iterative process. Regularly review and update the architecture to incorporate lessons learned, emerging technologies, and evolving threats. Monitor the effectiveness of security controls and adapt them as needed to ensure ongoing protection.
By following these best practices, organisations can establish a robust and effective security architecture that addresses their unique needs, mitigates risks, and protects critical assets and operations.
Why security architecture is crucial for your business: a conclusion
Security architecture is crucial for businesses as it provides a comprehensive, proactive, and strategic approach to security. It helps protect assets, mitigate risks, ensure compliance, maintain business continuity, build trust, reduce costs, enable growth, and foster a security-focused culture. By investing in a robust security architecture, organisations can establish a strong security posture and effectively navigate the ever-evolving threat landscape.
Keen to learn more or start the process of optimising your security architecture? Do get in touch – our team of experienced security architects will be happy to look into your company and propose the best solutions to help you stay protected at all times.