What is a vulnerability assessment and how to identify security vulnerabilities?
As much as one out of ten vulnerabilities in internet-facing applications are considered high or critical risk. How to identify them, how to protect your business against them and what's the role of a vulnerability assessment?
According to the latest Edgescan’s 2022 Vulnerability Statistics Report, as much as one out of ten vulnerabilities in internet-facing applications are considered high or critical risk. How to identify them, how to protect your business against them and what’s the role of a vulnerability assessment? Let’s find out!
What is a vulnerability assessment?
A vulnerability assessment is a process of identifying, quantifying and prioritising vulnerabilities in a system, network or application. It involves evaluating the security of a system by searching and identifying weaknesses that could be exploited by cybercriminals. As such it is an essential part of any effective security programme and helps organisations identify and address security risks that require attention.
A few examples of security vulnerabilities
To better understand the importance of a vulnerability assessment, let’s look in more detail at security vulnerabilities that can put organisations at significant risks. The most popular ones include weak passwords, unpatched software, social engineering, SQL injections, cross-site scripting (XSS) or misconfigured servers. What’s important, those and other vulnerabilities can exist in any areas of an organisations’ IT infrastructure and must be addressed to ensure a strong security posture.
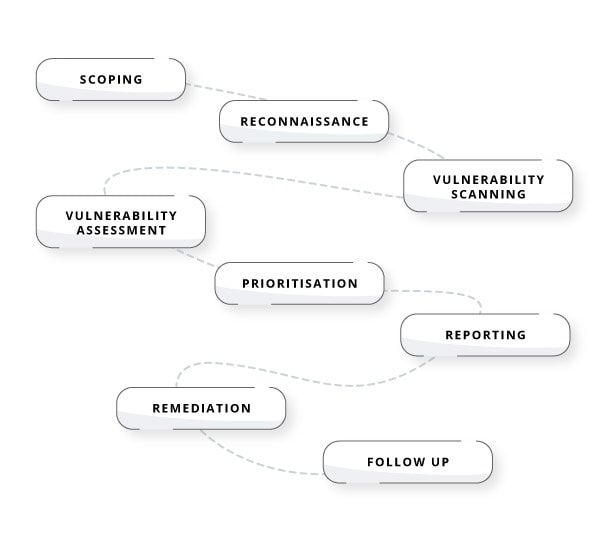
What is included in a vulnerability assessment?
A vulnerability assessment typically consists of the following steps:
- scoping, meaning defining the scope and objectives of such an assessment,
- reconnaissance, involving gathering information about the system or network,
- vulnerability scanning, used to identify potential security weaknesses in the system,
- vulnerability assessment – a process when identified vulnerabilities are analysed to determine their potential impact,
- prioritisation, meaning grouping vulnerabilities depending on their severity, their potential impact and the likelihood of them being exploited,
- reporting, which summarises all the findings and includes recommendations for remediation,
- remediation, meaning actions that need to be taken to remediate identified vulnerabilities,
- follow up, meaning conducting regular vulnerability assessments to ensure the system is safe long-term.
Types of vulnerability assessments
There are many types of vulnerability assessments, and some of them include:
- network vulnerability assessment that focuses on identifying potential security risks in a network infrastructure,
- web application vulnerability assessment that involves identifying potential security risks in web applications,
- desktop vulnerability assessment that identifies potential security risks within desktop applications,
- mobile app vulnerability assessment that aims at identifying potential security risks within mobile apps.
Vulnerability assessments and penetration testing (VAPT)
When talking about vulnerability assessment it is important to mention also VAPT – Vulnerability Assessment and Penetration Testing. It’s a type of security testing used to identify vulnerabilities in computer systems, network and application, composed of two processes: vulnerability assessment and a penetration testing. The latter one involves attempting to exploits vulnerabilities to gain access to sensitive information, system or networks, by simulating a hacker’s attack.
VAPT is an important process for organisations to ensure the security of their systems and networks, and to prevent data breaches and other security incidents.
When should I perform a vulnerability analysis?
Performing a vulnerability assessment is an essential step in maintaining the security of every organisation’s IT infrastructure. Consider performing it in the following cases:
- regularly, as a part of a scheduled assessment to ensure all vulnerabilities are found and addressed on time,
- before going live with a new application or when delivering new functionality; VAPT/VA should be included into every delivery process and pentest activities should be done regularly during every development process,
- after major changes to your organisation’s infrastructure, such as an installation or upgrading of a new software or changes in the data that you store,
- before implementing new systems, to identify potential weaknesses and to make sure you’ve got the right security level,
- after every security breach, to determine how it happened and check for other vulnerabilities that could be exploited,
- when needed for compliance requirements.
The importance of vulnerability assessment
By allowing you to be on top of potential vulnerabilities of your system, vulnerability assessments are an essential part of security programme of every organisation. Regular vulnerability assessment can help organisations proactively address security risks before they get exploited by hackers, allowing for improved security posture and saving time and money related to mitigating breaches that have already happened – bugs and vulnerabilities found during development process are less costly than those that needs to be fixed on production or when compared to cost of data breach.
What’s more, according to the new NIS2 directive – the Network and Information Security Directive 2 agreed by the European Council and European Parliament, which places a number of cybersecurity requirements on operators of essential services and relevant digital service providers – penetration testing and VA will soon be an obligatory compliance requirement for all companies under NIS2.0 regulations.
At Future Processing we know exactly how to help our customers get ready for all those changes and how to improve their security posture. Get in touch with us today to speak about any cybersecurity-related issues you want to discuss.