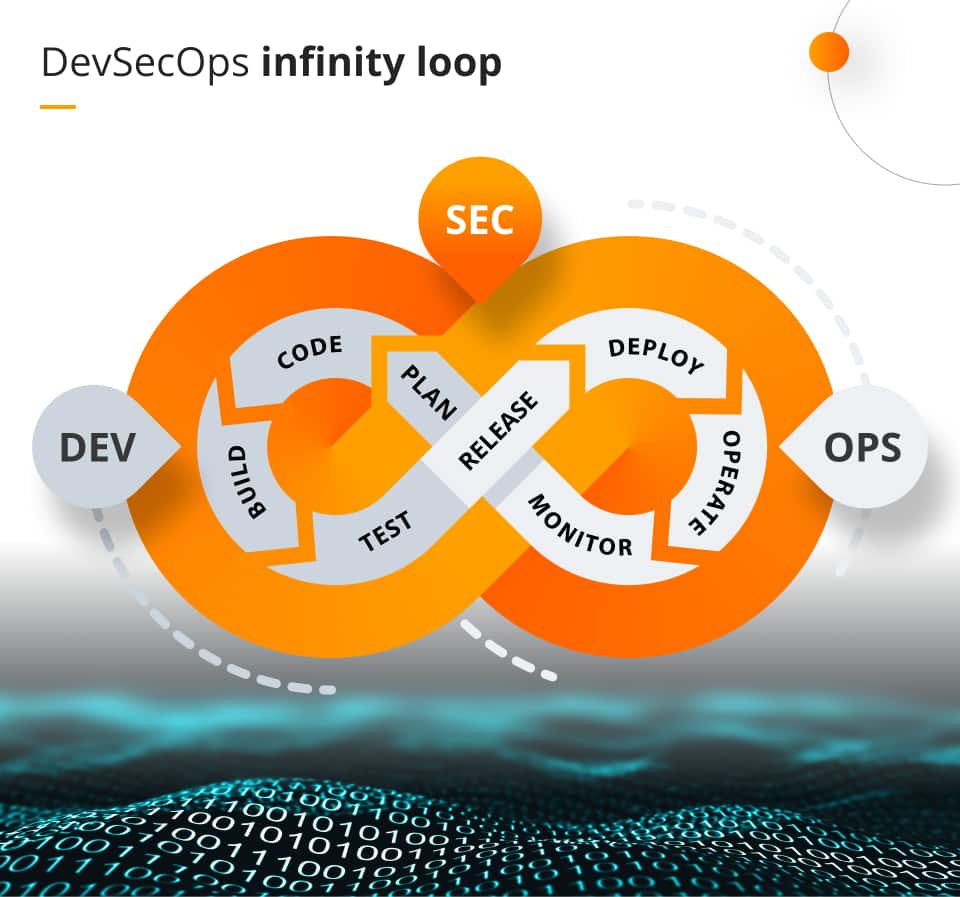
What is SecOps (Security Operations)?
Security operations is a combination of both security and IT operations staff with the goal of assessing and monitoring security risks and protecting corporate assets.
SecOps (also known as Security Operations) is the practice of combining IT security and operations teams to collaborate on security-related initiatives. This includes the integration of security tools, processes and practices into the DevOps workflow. SecOps teams work together to ensure that security is built into the development process from the start and that the application, systems and networks remain secure in production.
What is security operations (SecOps)?
Security operations is a combination of both security and IT operations staff with the goal of assessing and monitoring security risks and protecting corporate assets.
In recent years, cybersecurity attacks have been on the rise. The CrowdStrike 2023 Global Threat Report noted that compared to 2021, in the year 2022, there was a 50% increase in interactive intrusion campaigns and a 71% in adversary tactics (up from 62% in 2021). The report goes on to say that there was a huge increase in criminal activity, and identified more than 2,500 advertisements for access across the criminal underground, representing a 112% increase compared to 2021 and demonstrating a clear demand for access to broker services.
For companies, staying on top of the constant threat of attacks is very time-consuming and expensive. In order to mitigate these risks and reduce costs, companies are relying more heavily on SecOps teams to assist them to hunt down and eliminate potential cyber threats more effectively.
Why is SecOps important?
The importance of IT security teams is greater than ever. However, as their role expands, it can produce a gap between the IT security and IT operations teams. Both teams have different fundamental priorities, which often results in them pulling in different directions. This can create inefficiencies, reduce the effectiveness of security measures and expose the organisation to greater risks.
An example of this would be when the company’s security tools shut down or block critical applications to reduce risk, but the applications are running time-sensitive operations which are disturbed by the interruption – one operation working independently of the other causes interference.
SecOps, as the marriage between IT security and IT operations, allows both teams to work together more closely, with both teams sharing full accountability for maintaining the company’s security, as well as the productive state of operations.
By working together, there is greater visibility of security vulnerabilities throughout the entire organisation, with critical information being shared quickly and effectively to help reduce security issues while simultaneously keeping IT operations fully functioning and agile.
What are the goals and benefits of SecOps?
The goal of SecOps (Security Operations) is to reduce the risk posed to an organisation’s IT infrastructure by implementing automated security processes and procedures.
The primary benefit of SecOps is that it creates collaboration across multiple teams within an organisation, which enables them to quickly identify and respond to potential security threats, thereby reducing the risk of data loss and systems’ downtime.
Security operations also help to increase the visibility of the company’s security infrastructure in order to create stronger security practices that will be more effective long term.
SecOps helps to ensure that management is involved at all levels, which helps to create a roadmap aimed at increasing and improving the organisation’s security without compromising the overall performance.
Finally, it can help organisations become more efficient and cost-effective by automating and streamlining security operations.
Examples of the benefits of SecOps
It is clear that there are lots of useful benefits that SecOps can bring to a company’s operations. Two very effective SecOps examples that companies regularly use are SAST and DAST:
Static Analysis Security Testing (SAST)
SAST allows developers to find any security vulnerabilities that are actually within the application source code much earlier in the software development life cycle. In addition, it ensures that your operations conform to the necessary coding guidelines and standards while not actually executing the underlying code.
Dynamic Analysis Security Testing (DAST)
While similar to SAST, DAST allows SecOps teams to find any security vulnerabilities that may be present within applications that are actually running (as opposed to SAST which looks at the source code). Typically, this mostly applies to web applications.
Dynamic Analysis Security Testing finds these vulnerabilities by employing fault injection techniques in an app using methods such as cross-site scripting (XSS) or SQL injection. It feeds malicious data right into the software in order to be able to identify any potential vulnerabilities.
DAST also has the ability to identify runtime issues that couldn’t otherwise be identified using static analysis security testing techniques, for example, flaws that are only visible when a known user logs into the system, or any authentication and server configuration issues.
SAST and DAST – Co-dependent operations that are often used in tandem
Commonly, both SAST and DAST are used in conjunction with one another by SecOps teams. They both have flaws that cannot be overcome alone, but by using them both together, SecOps teams are able to gain a full picture of their security vulnerabilities.
For example, SAST isn’t an effective technique for discovering runtime errors and DAST is not likely to flag any coding errors (that goes to say, at least not in terms of the code line number). Conversely, SAST performs rather well when it comes to finding line code errors like weak code generation (e.g. weak random number generation), but it is not great at uncovering flaws in the data flow. SAST is also very well known for generating a higher number of ‘false positives’, or in other words, less likely to result in ‘false negatives’.
Both SAST and DAST solutions are used in tandem by SecOps teams to very effectively enhance a company’s security operations.
What are some best practices for implementing SecOps?
When implementing SecOps into an organisation, it is important to follow tried-and-tested practices to maximise its impact and reduce any potential issues.
Here are some best practices for implementing SecOps:
- Defining the scope of SecOps – This helps to focus on the needs of the company and to narrow down what has to be done to protect it.
- Creating reusable workflows – The SecOps team faces a variety of challenges across the entire company. Each security process created can only address a very specific threat, but the SecOps team can optimise their solutions by making them as broad as possible, ensuring that they are reusable and can be reconfigured to deal with other types of threats at a later time.
- ‘Real-life’ training activities – Just as a well-trained military force remains active and fully prepared through ongoing training and simulations, the SecOps team can run simulated ‘attacks’ to help hone their skills and response procedures. One team can ‘attack’ the systems, while the SecOps team ‘defends’ – this helps keep the team sharp, prepared, and tests their ability to respond quickly and effectively.
- Process automation – Automation is very important to implementing SecOps effectively, especially across large organisations. Automation not only reduces the number of tasks that need to be done by a human, but it also allows for better real-time monitoring and incident response.
- Incorporating security throughout the organisation – The SecOps team identifies and responds to threats all throughout the delivery pipeline (as opposed to a traditional security team who typically focuses on threats received on already deployed applications). This allows security teams to identify and respond to threats early on, meaning developers can write new code quickly and have the system constantly monitoring for new vulnerabilities and bugs.
Summary
SecOps, the natural progression from the development processes into a more highly integrated security solution that crosses company-wide departments, allows for much greater risk protection. It is certainly more complex to integrate into an organisation. Still, when done well, the organisation benefits from greater real-time awareness of issues, better communication and less downtime between departments and operations, reduced costs, and overall greater ability to respond to risks. It is undoubtedly crucial for companies in this modern world.